Working with Visa APIs
Here are a few ways to get started and learn about end-to-end process around engaging with our APIs and building a new project.
Read our Quick Start Guides
Our quick start guides will take you through the step-by-step process and point the way towards the detailed documentation as you need it.
For Developers
This guide is for you if you are looking for the technical walk through of adding Visa APIs into your product.
For Business Users
This guide provides details on how and why to work with Visa, as well as availability and pricing framework of our APIs.
Understand the Visa Developer Platform Technology Architecture
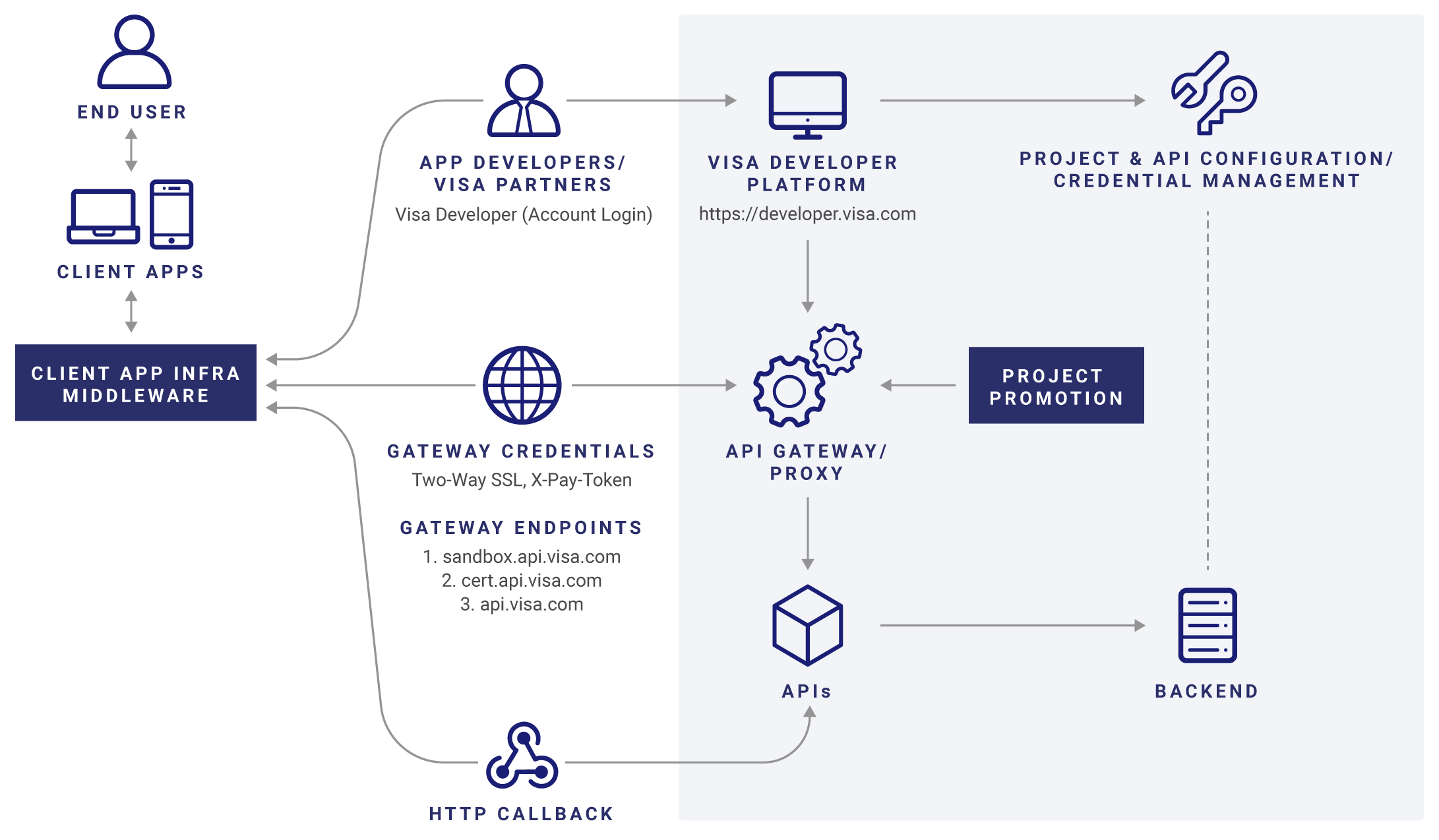
Visa Developer Platform helps consolidate multiple partner and developer facing assets across Visa into a common platform to simplify partner connectivity. Visa’s API management features can help accelerate the pace of collaboration and innovation within Visa and between its strategic partner, by providing them with a one stop shop for API availability. The API management platform becomes an API “portal” where developers across the B2B/B2C space can efficiently leverage Visa APIs.
Explore the Documentation
Here are some helpful links. Browse all documentation to see a full list of guides and resources for using Visa APIs.
